Transportation Management Center Information Technology SecurityChapter 3. Best Practices for Traffic Management Centers Information Technology SecurityBest Practices DiscussionWhile synthesizing the available resources on Intelligent Transportation Systems (ITS) cybersecurity, sources from the Department of Homeland Security (DHS), the Center for Internet Security (CIS), and the National Institute of Standards and Technology (NIST) were considered for their relevance to Traffic Management Centers (TMC). Several agencies acknowledged and referenced the use of the NIST Cybersecurity Framework, while others used other agency directives to guide their control strategies. As a result of evaluating these different standards, some common themes were identified, including:
From the analysis, it was determined that the NIST Cybersecurity and Risk Management Frameworks were more abstract and strategic in nature, while the CIS Top 20 Controls provide more technical detailed guidelines of immediate benefit to TMC operators. Thus, using the CIS Top 20 Controls in baselining security measures provides an immediate impact on guiding control of hardware, software and networks in the TMC, while the NIST frameworks can play a beneficial role to supplement with strategic visioning of Risk Management Plans and Resiliency Plans. The purpose of this report is not to replicate the guidelines in these frameworks, but rather to highlight the guidelines most relevant to TMC IT cybersecurity. Risk management begins with the awareness of what vulnerabilities the TMC is exposed to, based on the characteristics of the staffing (employees and contract staff), the types of devices and how they are connected to the network, and the software used throughout to control and management operations. Cybersecurity self-assessments for the organization also are discussed as a prioritization strategy in chapter 5. Implementing CIS Top 20 building blocks for Internet security provides a layered approach to addressing all areas of risk exposure. The CIS Controls are separated into Basic, Foundational, and Organizational levels of IT security management. A complete list of the controls for IT security is provided in figure 4 below. Controls that can be applied to TMC IT/OT security will be discussed in further detail in subsequent chapters. 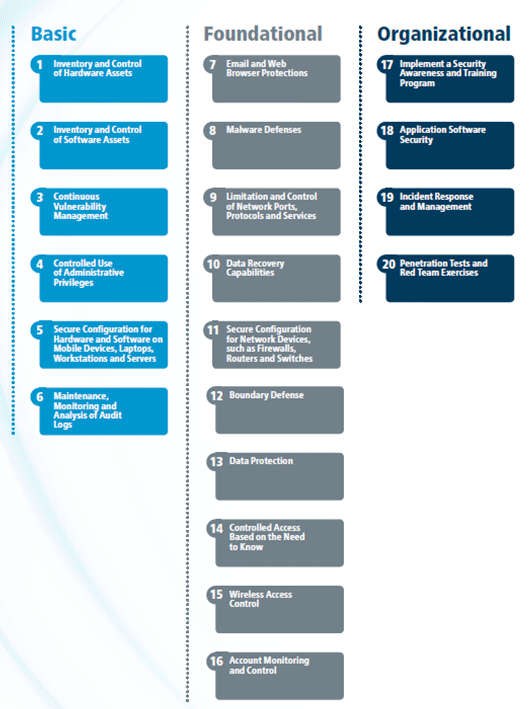 Figure 4. Chart. Center for Internet Security top 20 critical security controls version 7.1. (Source: CIS Controls Version 7.1.) The National Institute of Standards and Technology Risk Management FrameworkAs a primer to establishing the TMC IT Security guidelines in this report, it is worth a quick review of the NIST Risk Management Framework for conducting cybersecurity risk management. This framework provides a set of six (6) steps for managing risk, which are shown within the inner-circle of the figure below. The figure from NIST SP 800-37 illustrates the risk management process in context with other Federal Information Processing Standards (FIPS) and other Special Publication (SP) references.4 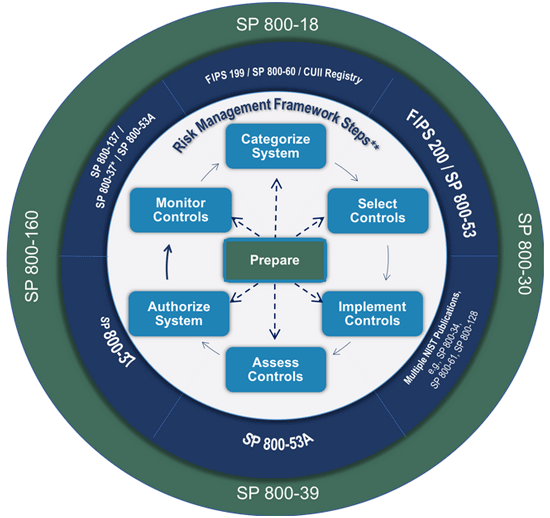 Figure 5. Flowchart. The National Institute of Standards and Technology risk management framework. (Source: NIST SP 800-37 Risk Management Framework.) As this is the most well documented risk management methodology proposed by the Federal Government, it is directly applicable to any TMCs that choose to pursue a risk management-based cybersecurity strategy. Some agencies, particularly those with connections to the Federal sector also will need to stay apprised of NIST 800-53 (for Federal information systems/organizations) and FedRAMP (for cloud hosting).5 While this document focuses on broader guidelines for TMCs, some organizations may find the NIST documentation helpful in evaluating, selecting and specifying information systems or controls for subsystems within the TMC environment. Two relevant NIST documents will be useful for supplementing CIS Top 20 for chapters 8 and 9 for administrative policies and resiliency plan development:
Additionally, while most TMCs do not process billing information for credit cards associated with tolling or fare collection systems, it should be noted that agencies having this responsibility also are obligated to comply with Payment Card Industry Data Security Standards (PCI–DSS) for processing back-office toll payments and other credit card financial transactions. The goals of PCI DSS are compatible with NIST Cybersecurity Framework and CIS Top 20, and are built to maintain a secure network, protect cardholder data, maintain a vulnerability management program, implement strong access control measures, regularly monitor and test networks, and maintain an information security policy. Best Practices Scan of Traffic Management Center OperatorsThis section will summarize noteworthy practices identified by agencies responding to the questionnaire and existing reference literature and correlating them to the CIS Top 20 controls. During a scan of several TMC operators across the country of varying sizes, the following cybersecurity practices currently are being employed by one or more organizations:
Gaps/Areas of ImprovementMore so than trends, the review of several TMC operators during the survey process gave indication of notable areas in need of improvement within the industry. The following areas of concern have been identified, along with the importance of each, though they are not necessarily widespread issues for all organizations:
The Role of Construction/Procurement Methods in Traffic Management Center Information Technology SecurityTransportation agencies are subject to public procurement guidelines and are accustomed to designing projects and putting them out to bid. However, the TMC environment and the IT portion of that environment have increasingly become classified as sensitive or critical infrastructure information to be guarded from the public domain. Agencies should have policies and guidelines in place for determining what aspects of their construction plans qualify as sensitive information and manage the procurement accordingly. For instance, some agencies establish on-call contracts with vetted contractors that also have executed non-disclosure agreements, and only issue work orders for upgrades to the network or the facility to prevent sensitive information entering the public domain. Others will issue a two-step Invitation for Bid (IFB) to pre-qualify potential contractors before releasing copies of the plans to them. These are examples of the use of procurement methods to mitigate the risks associated with exposing a TMC's critical infrastructure information in the public domain. Relegating the configuration settings for network devices to installation contractors also should be verified to ensure adherence to TMC network configuration policies identified with CIS Controls. When possible, TMC IT staff should provide configuration files and prevent alterations of those configurations instead of leaving it to the contractors to maintain control of the hardware, software, and network assets in the TMC. Supply chain attacks against hardware and software vendors are becoming more common. Procurement through reputable sources are a minimum best practice but establishing pre-negotiated periods for responding to security issues with upgrades/patches is an important consideration for procurement of software and hardware contracts, particularly for specialized equipment related to ICS vendors. Additionally, this and other examples of cybersecurity procurement language for control systems has been provided for various subsystems by U.S. Computer Emergency Response Teams (US CERT).7 Many medium-to-large TMCs use a dedicated/isolated test environment to validate upgrades and patches before loading into the production environment to minimize risks from supply chain. 4NIST, "SP 800-37 Rev. 2 Guide for Applying the Risk Management Framework to Federal Information Systems: a Security Life Cycle Approach," 2018. Retrieved from: https://csrc.nist.gov/publications/detail/sp/800-37/rev-1/final. [Return to footnote 4] 5NIST, "SP 800-53 Rev. 4 Security and Privacy Controls for Federal Information Systems and Organizations," 2015. Retrieved from: https://csrc.nist.gov/publications/detail/sp/800-53/rev-4/final. [Return to footnote 5] 6NIST, "SP 800-82 Rev. 2 Guide to Industrial Control Systems (ICS) Security," 2015. Retrieved from: https://csrc.nist.gov/publications/detail/sp/800-82/rev-2/final. [Return to footnote 6] 7Department of Homeland Security (DHS), "Cyber Security Procurement Language for Control Systems," 2009. Retrieved from: https://ics-cert.us-cert.gov/sites/default/files/documents/Procurement_Language_Rev4_100809_S508C.pdf. [Return to footnote 7] You may need the Adobe® Reader® to view the PDFs on this page. |
|
United States Department of Transportation - Federal Highway Administration |
||