Transportation Management Center Information Technology SecurityChapter 4. Technical Guidelines and Recommended PracticesThis section provides the introduction to the technical guidelines and recommended practices in chapters 5 through 9, which build a culture of Operations Technology (OT)/Information Technology (IT) security for Traffic Management Centers (TMC); keeping it at the process/organizational structure level and related to the National Institute of Standards and Technology (NIST) Cybersecurity Framework (CSF) and Center for Internet Security (CIS) Top 20 Controls. The NIST Cybersecurity Framework provides guidelines for how organizations can assess and improve the ability to secure their environments, manage risk, and respond to threats. The five areas for NIST Cybersecurity Framework core functions are as follows:
The CIS Top 20 were developed to provide organizations with a smaller, prioritized number of actionable controls that should be implemented first. The CIS Top 20 outline Critical Security Controls (CSC) that organizations can use to establish a baseline for protection of their environment. A TMC environment, along with supporting staff, is typically comprised of individuals with distinct roles focused on managing three areas:
The CIS Top 20 Critical Security Controls correspond to these three functional areas, and each CIS sub-control is relevant to one of the three TMC roles. The first TMC role, which is subdivided to address hardware, software, and networking within the overall information technology management area, will be covered in chapters 5, 6, and 7, respectively. Chapter 8 highlights guidelines relevant to personnel controls and elements associated with insider vulnerabilities. Chapter 9 covers controls associated with data protection and resiliency. The figure below shows the CIS controls that are relevant to each of these TMC roles. They have been color-coded to match the Basic, Foundational, and Organizational control labeling in the CIS document figures shown in chapter 3. 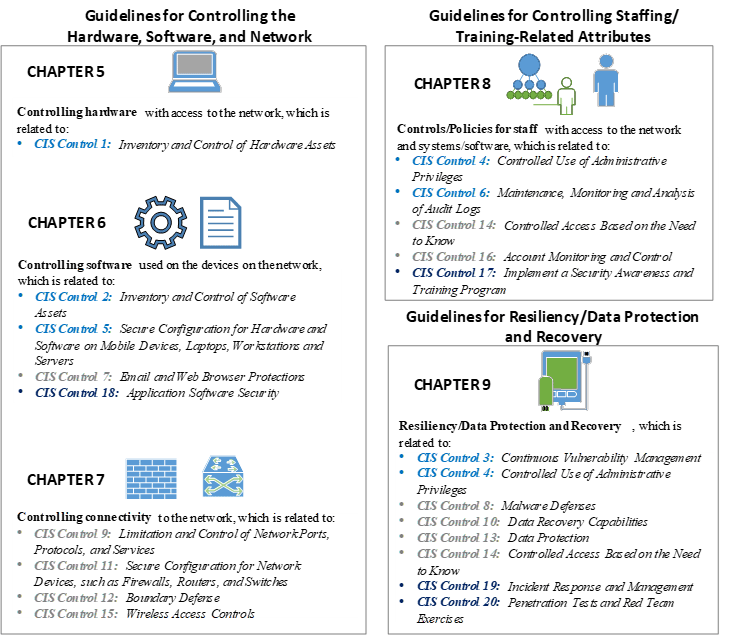 Figure 6. Chart. Relationship between Center for Internet Security Controls and Traffic Management Center roles. (Source: Federal Highway Administration.) While the predominant focus of these guidelines is on the CIS Controls, mapping between CIS and NIST has been developed by CIS and can be used by organizations focusing in one set of controls or the other.8 In the appendices, a full copy of the CIS to NIST mapping is printed based on the current date of this report. However, users of these guidelines are encouraged to go to the CIS Controls website for the most current version. A subset of CIS Control 1 is provided below as a reference for the associated cross-mapping. A summary table of the controls associated with each topic area in chapters 5 through 9 has been provided at the end of each topic, focusing on the relevant CIS controls. Agencies that already are involved with the use of NIST are advised to reference the appendices for the complete list of associated NIST CSF activities associated with the recommended CIS Controls documented herein. 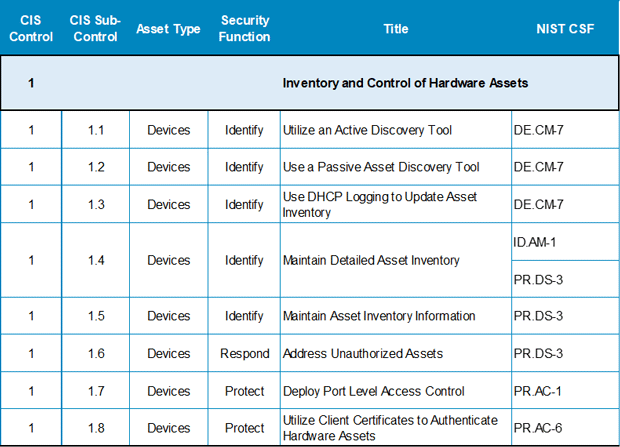 Figure 7. Screenshot. Center for Internet Security controls mapping to the National Institute of Standards and Technology security functions and the National Institute of Standards and Technology cybersecurity framework. (Source: CIS Controls Version 7.1.) Additionally, DHS has developed a similar mapping document to map NIST controls to Cyber Resilience Review (CRR) controls.9 The emphasis on CIS Controls provides a central approach that can be used throughout these guidelines, and readily accommodates cross-referencing between the other frameworks for additional supporting information. While it will not eliminate all risks, using the following guidelines can provide ways to manage and control those risks. Relevant CIS Top 20 Controls are incorporated into each subsection as noted above. CIS Controls version 7.1 has been structured in layers based on an organization's size and sophistication. The following diagrams from v7.1 shows three levels of organizational capabilities. 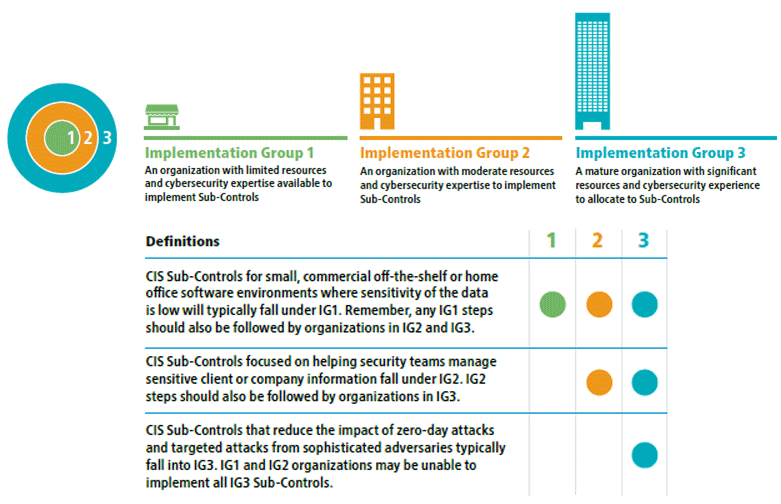 Figure 8. Infographic. Center for Internet Security implementation groups. (Source: CIS Controls version 7.1.) Within the CIS Controls document, as the organization reviews recommendations for protecting the TMC, priority should be given to those that are recommended for all three implementation groups, followed by those recommended for groups 2 and 3, and finally those applicable to just group 3. It is anticipated that the majority of TMCs will fall into group 2. Some smaller organizations will fall into group 1. Larger organizations, or those abiding within regulatory scrutiny, will fall into group 3. For TMCs, since the primary recommendation is to follow CIS Controls for initial guidelines, this section will focus heavily on each of those CIS Top 20 Controls. Within each CIS Control, the sub-controls focus on a type of asset (e.g., Users, Networks, Applications, Devices, and Data), and the security function (e.g., Identify, Protect, Detect, Respond), which correlate to NIST Cybersecurity Framework elements. 8Center for Internet Security (CIS), "CIS Controls V7.1 Mapping to NIST CSF." Retrieved from: https://www.cisecurity.org/white-papers/cis-controls-v7-1-mapping-to-nist-csf/. [Return to footnote 8] 9Department of Homeland Security (DHS), "Cyber Resilience Review (CRR): NIST Cybersecurity Framework Crosswalks," 2016. Retrieved from: https://www.us-cert.gov/sites/default/files/c3vp/csc-crr-nist-framework-crosswalk.pdf. [Return to footnote 9] You may need the Adobe® Reader® to view the PDFs on this page. |
|
United States Department of Transportation - Federal Highway Administration |
||