Transportation Management Center Information Technology SecurityChapter 2. Critical Traffic Management Centers ElementsAn important aspect of cybersecurity frameworks is that both devices and personnel must be secured. Both the National Institute of Standards and Technology (NIST) Cybersecurity Framework and the Center for Internet Security (CIS) Top 20 Controls underscore this importance.2, 3 In the Traffic Management Center (TMC) context, this involves identifying field devices, central systems and staff composition. The complexity of the organization and the systems being managed play a prominent role in determining TMC Information Technology (IT) Security Guidelines. The NIST Cybersecurity Framework and the CIS Top 20 Controls ultimately are comprised of recommendations for controlling hardware with access to the network, controlling software used on the devices on the network, controlling connectivity to the network, implementing controls and policies for staff with access to the network, systems and software, and ensuring resiliency, data protection and recovery. This chapter will set a baseline for typical TMC composition as it relates to TMC IT security. Beyond Knowing/Identifying the TMC Critical Elements, other aspects of the Cybersecurity Framework functions will be discussed in subsequent chapters. TMCs vary in size, responsibility, and complexity. As a result, there is no one-size-fits-all approach to cybersecurity. To capture the differences among TMCs and to obtain a baseline for prevailing practice, a Cybersecurity Maturity Questionnaire was distributed to TMCs of diverse types and sizes across multiple States to identify similarities and differences among various agency IT models and settings. Seventeen (17) complete responses were received from the following agencies:
Due to the sample size, the discussion and analysis of responses is not intended to be a statistically significant representation of cybersecurity practices. Rather, the results are intended to capture the diversity of TMC sizes and responsibilities around the United States, to reveal areas of commonality and difference, to suggest areas in which the industry is doing well, and to suggest opportunities for improvement. A summary of the ways in which TMCs are characterized and categorized is included in this chapter. Best practice recommendations for TMC IT cybersecurity as they relate to these elements are included in subsequent chapters. Size and StaffingFor classification purposes, the questionnaire asked respondents to self-assign their agency into one of three size categories: small, medium, or large. Large TMCs were categorized as TMCs with more than 10 operators during peak hours who manage over 500 devices. Medium sized TMCs had between 5 and 10 peak-hour operators who managed between 100 and 500 devices, and small TMCs had less than 5 peak-hour operators who managed less than 100 devices. Of the respondent agencies, one (1) self-identified as small, seven (7) as medium, and nine (9) as large. In addition to staff size, it is important to be aware of staff composition and the security impacts associated with various staff types. Of the agencies surveyed, approximately half did not have any IT staff dedicated to the TMC, some had shared IT between different agency departments, some were dedicated but part of a separate centralized department serving the entire agency, and some had dedicated staff within the department. Furthermore, approximately half of the agencies surveyed reported that their IT was centrally managed, with the remaining half being managed by contractors or a combination of central staff and contract staff. No direct correlations were apparent between the staff mix versus the size or complexity of the TMC environment. ResponsibilitiesA TMC may be responsible for managing freeway operations, arterial highway operations, heavy rail operations, transit operations, or a combination of these. A TMC's focus may be urban or rural, regional or statewide. It may be single or multi-jurisdictional. TMC staff also may partner with other agencies to cover these variety of transportation networks, including police and transit. TMCs employ any combination of the responsibilities below:
Device and Network ManagementTMCs utilize a range of devices and equipment to collect data, disseminate information, and control operations. These devices require initial programming, ongoing maintenance and software updates, and in most cases, some means of data exchange with each other and/or the TMC. To that end, a variety of communications methods are common in the industry. A graphical depiction of these relationships developed by the United States Department of Transportation (USDOT) is shown in the figure on the following page. 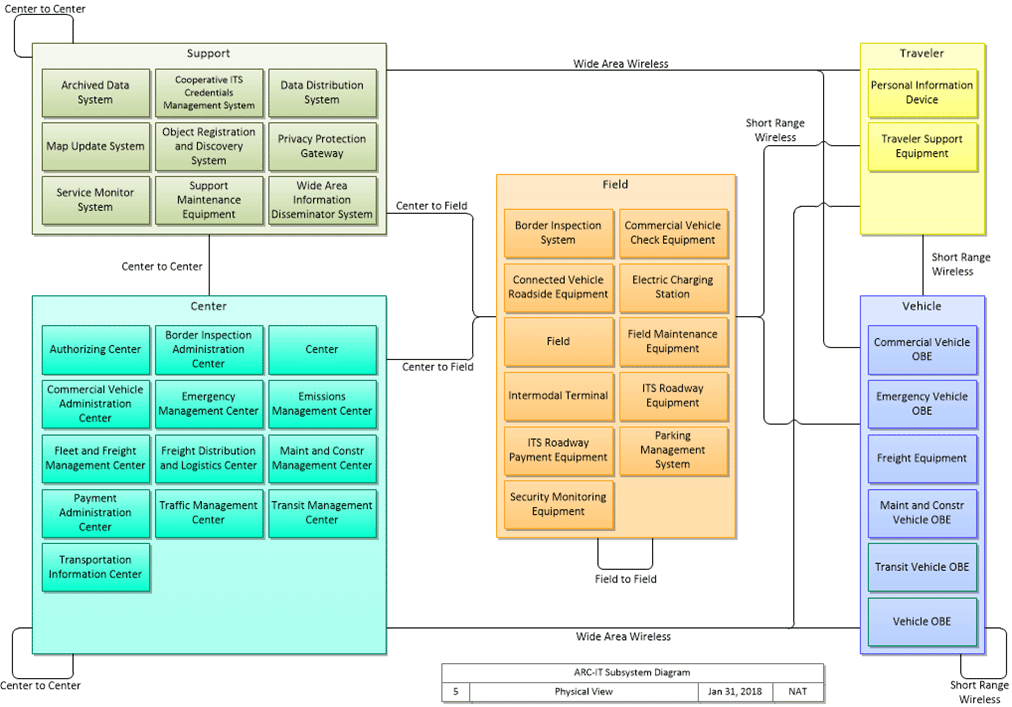 Figure 3. Flowchart. National Intelligent Transportation System architecture physical view. (Source: National Intelligent Transportation Systems (ITS) Architecture.) In the figure above, "wide area wireless" and "short range wireless" are two of the many communications types that may be utilized by a TMC for Center-to-Center, Center-to-Field, and Field-to-Field communications. Communications types commonly utilized by TMCs across the United States include twisted pair copper cable, fiber optic cable, licensed and unlicensed point to point or point to multi-point wireless, leased wired (i.e., broadband), and leased wireless (i.e., cellular) communications. Each of these types of communications provides its own security concerns, many of which will be discussed at a high level in future chapters. It also should be noted that some of these devices have limitations in the way they operate that make protection at the device difficult. For example, a wireless point to point radio transmitter is not housed in a locked enclosure and is exposed to potential tampering. In other cases, devices may be housed in a locked enclosure, but a series of standard physical keys may be shared across multiple agencies to access those enclosures. In most cases, devices or device groups access the communications network back to the TMC via network switches. It is important that these network switches/access points have security measures and encryption in place to control access to the system. To protect the overall system further, some TMCs have deployed firewalls and other controls to protect network boundaries and create network separation. This is especially important between the field environment and the TMC environment. Some TMCs have multiple servers and/or off-site data storage or backup to provide an additional layer of separation and redundancy. 2NIST, "Risk Management Framework for Information Systems and Organizations," October 2018. Retrieved from: https://csrc.nist.gov/publications/detail/sp/800-37/rev-2/archive/2017-09-28. [Return to footnote 2] 3Center for Internet Security (CIS), "CIS Controls Version 7.1," 2019. Retrieved from: https://www.cisecurity.org/controls/. [Return to footnote 3] |
|
United States Department of Transportation - Federal Highway Administration |
||