Enhancing Active Transportation and Demand Management (ATDM) with Advanced and Emerging Technologies and Data SourcesChapter 6. Operations and Maintenance ConsiderationsThis chapter provides insight into the considerations for operation and maintenance (O&M) as it relates to emerging technologies and data sources. Routine O&M maintenance will be different due to the very nature of these technologies as will other areas such as cybersecurity and data privacy, performance monitoring and maintenance, enforcement, O&M costs, and future proofing. 6.1 Routine Operations and Maintenance IssuesOnce the new and/or enhanced ATDM solutions go online, there are a host of O&M issues to deal with. Some items for consideration include performance monitoring, routine maintenance, enforcement, and costs. Moreover, many of the emerging technologies and data sources discussed in this Reference require critical O&M considerations. Some investigations of active transportation and demand management (ATDM) O&M issues have already been published. One example is the ATM Implementation and Operations Guide, which provides a full chapter on O&M.(17, 37) Some O&M principles discussed here (e.g., necessary data, levels of automation, common performance measures, typical O&M costs, post-project evaluation) are likely relevant to the newer technologies and to the broader ATDM scope. The ATDM Lessons Learned report described numerous real-world implementations, some of which cited maintenance as a significant dis-benefit.(62) The technical brief on Data Needs for ATDM (11) discussed the data needs for monitoring and evaluation. The brief says that, although ATDM operations objectives are inextricably tied to performance measures (e.g., travel time, delay, planning time index), supplementary data should also be collected to understand the impacts of exogenous factors (e.g., price of fuel, unemployment rates, other highway improvements, work zones). The Guide for Highway Capacity and Operations Analysis of ATDM Strategies: Analysis of Operational Strategies under Varying Demand and Capacity Conditions (23) highlights the importance of nonrecurring event data and of forecasting the various percentile outcomes (e.g., expected 80th and 95th percentile worst performance). Cybersecurity and Data PrivacySome of the emerging technologies and data sources present some unique cybersecurity and privacy concerns. Many of today's ATDM systems are relatively "closed" from the standpoint that they communicate with sensors, devices, and external systems that are on the agencies' private network. Some of these newer technologies and data sources are connected with outside "uncontrolled systems" and in their nature may have some data privacy considerations. The particular ones that should be noted include:
For enhancing ATDM through emerging technologies and data sources, many of the primary O&M considerations involve management and security of data. The FHWA Reliability Data Guide's section on data ownership and maintenance presented a sample list of fundamental considerations likely to govern O&M levels of effort and expense: (30)
CAVs are a key quadrant of emerging technology that gain a lot of attention as it relates to cybersecurity (access to a vehicles bus) and data privacy (data that can be potentially used to track vehicle locations). Some ATDM solutions (e.g., multi-modal intelligent signal systems, integrated dynamic transit operation) are specifically designed to exploit CAV technology. Archiving, documentation, and analysis of the resulting data may be critical to the success of such deployments. A presentation entitled "Sharing Connected Vehicle Data on the Research Data Exchange (RDE)" addressed some of the challenges and opportunities associated with high-volume multi-source data from CAV, connected travelers with mobile devices, and other sources.(43) Figure 23 illustrates some of the O&M activities needed to enable CAV benefits. 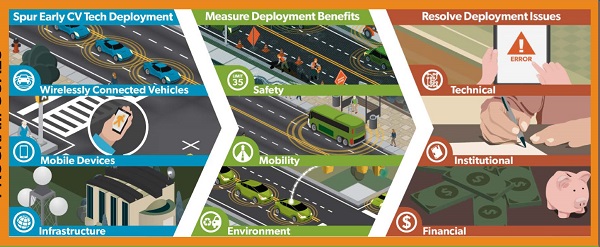 This screenshot depicts the linkage between connected and automated vehicle goals and operations and management issues by showing three sections that start with Spur early connected vehicle tech deployment, next comes measure deployment benefits, and finally resolve deployment issues. The spur early connected vehicle tech deployment section includes wirelessly connected vehicles shown as cars with wireless signals,, mobile devices showing a hand holding a wireless phone, and infrastructure showing a building that can receive signals via a signal receiver dish. The measure deployment benefits section includes safety showing a road with signs and pedestrians, mobility showing a bus with a wireless signal, and environment showing vehicles communicating with the surrounding infrastructure. The resolve deployment issues section includes technical showing a hand-held device, institutional showing an individual creating a report, and financial showing money and a piggy bank.
This screenshot depicts the linkage between connected and automated vehicle goals and operations and management issues by showing three sections that start with Spur early connected vehicle tech deployment, next comes measure deployment benefits, and finally resolve deployment issues. The spur early connected vehicle tech deployment section includes wirelessly connected vehicles shown as cars with wireless signals,, mobile devices showing a hand holding a wireless phone, and infrastructure showing a building that can receive signals via a signal receiver dish. The measure deployment benefits section includes safety showing a road with signs and pedestrians, mobility showing a bus with a wireless signal, and environment showing vehicles communicating with the surrounding infrastructure. The resolve deployment issues section includes technical showing a hand-held device, institutional showing an individual creating a report, and financial showing money and a piggy bank.
Figure 23. Screenshot. Linkage of connected and automated vehicle goals and operations and management issues. Source: FHWA Data security is a key component of data archiving. Vandervalk et al. suggest that working copies of databases maintained on primary servers be replicated in compressed formats at remote sites.(51) These daily backups, which do not reflect a binding legal requirement, ensure that the archive service can be rapidly returned to operation with no significant loss of data if a copy of the database is lost. Both the primary database server and the backup storage are located in climate-controlled machine rooms with uninterruptible power supplies and generator backup power, preventing data loss or gaps in data availability due to power outages. The working copy of the database is stored on a redundant array of independent disk devices, providing error detection, redundancy, and the ability to rebuild missing data upon device failures. Finally, hardware maintenance and security updates are provided for all computer systems by experienced systems administration personnel. The Real-Time Data Capture and Management State of the Practice Assessment and Innovations Scan addressed issues related to data capture, data management, archiving, and sharing collected data to encourage collaboration, research, and operational development and improvement.(44) The scan covers five industries: aviation, freight logistics, internet search engines, rail transit systems, and transportation management systems. The scan documented best practices in several areas which are outlined here for reference. Please note that the best practices are strictly voluntary and they are not legally binding. The scan documented the following best practices for access, security, and privacy:
The scan documented the following best practices for data storage and backup:
The scan documented the following best practices for O&M:
The scan documented the following best practice for critical failures:
Performance Monitoring and MaintenanceAs discussed in the ATM Implementation and Operations Guide, performance monitoring is an integral part of the active management cycle, which was illustrated in chapter 1.(17, 37) Performance monitoring is an ongoing internal process where system conditions and performance are examined and evaluated through data collected through interfaces with devices/equipment installed in the field as well as data feeds such as probe or crowdsourced data. Performance monitoring provides the data needed in the decision-making process. Deployment agencies use data and performance monitoring during strategy activation. Activations typically fall into one of two types of processes, automated systems and manual systems, which vary greatly in the strategy activation thresholds used. In some cases, a hybrid automated-manual process is used. ATDM deployments are often part of an agency's overall transportation management system, which is a complex, integrated amalgamation of hardware, technologies, and processes. System maintenance includes replacing worn components, installing updated hardware and software, tuning the systems, and anticipating and correcting potential problems and deficiencies. Maintenance includes the development and implementation of action plans for responding quickly, efficiently, and orderly to systemic failures, as well as having infrastructure and procedures for measuring and monitoring maintenance activities. An agency's maintenance strategy can dictate system design and must be considered in the planning phase to ensure that it will have the personnel or financial resources to adequately maintain the ATDM solution. The ATM Implementation Guide provides more specificity on performance monitoring for specific solutions.(17, 37) For example, the guide lists a of sample agencies who implemented automated thresholds for ramp metering activation. Such thresholds were typically a combination of mainline occupancy, mainline volume, ramp queue length, and/or ramp storage length. Threshold values may be updated periodically (i.e., monthly, quarterly, or annually) based on continued assessments of system performance. Because the effectiveness of short-term and long-term performance monitoring depends on the quality of data collected, having access to quality data is an important element of performance monitoring. Emerging technologies and data sources can augment performance monitoring in active traffic management (ATM), active demand management (ADM), and active parking management (APM). Active Traffic ManagementMany strategies activate at specific traffic congestion levels to prevent, mitigate, or delay the onset of traffic bottlenecks. To accomplish this, performance monitoring is critical to determining when strategies should activate. Some predictive strategies employ combinations of historical and realtime data. Bayesian models use real-time data to improve the accuracy of predictions based on historical data. Machine learning (ML) methods are able to fine-tune and improve these prediction algorithms over time. Beyond monitoring traditional metrics such as flows, speeds, and densities, inclusion of non-recurring event data (e.g., weather, incidents) can help to explain performance and improve predictions. In summary, ATM performance monitoring can be augmented through (1) fusion of historical and real-time data (e.g., Bayesian methods), (2) explicit use of non-recurring event data (e.g., weather, incidents), and (3) ML. To augment the ATM solutions as described above, emerging technologies can help to improve both the quality and quantity of available data, especially when compared and/or combined with more traditional forms of data. For example, probe data are now used extensively to obtain traffic performance metrics. Social media provides a source of incident data.(53) Dynamic message signs (DMSs) can display optimized sets of driver information based on enhanced data sets and learning methods. Some urban data sets, including both traditional traffic sensors (e.g., loops, cameras) and cutting-edge sensors (e.g., Bluetooth, GPS probe, parking), have been archived for a decade. These rich data sets allow learning of traveler behavior and in-depth understanding of non-recurrent traffic. They can be applied directly to predict traffic impact of planned and unplanned incidents and provide real-time decision making for traffic operations.(55) Figure 24 illustrates an example of this ATM augmented by emerging technologies.  Figure 24. Map. Dynamic network analysis and real-time traffic management for the Philadelphia Metropolitan Area. Source: © Wei Ma, Pinchao Zhang and Sean Qian (2016) Regarding O&M issues for ATM, quality control has been a concern for probe data. Agencies may wish to monitor the proportion of missing data over time within probe data sets. Along surface arterials, accuracy of probe data may be compromised by the proximity and influence of traffic signals. Also, the proportion of vehicles surveyed within probe datasets changes over time and may become unacceptably low in some areas. Beyond probe data, weather and incident data may be less accurate on certain roadway segments. In summary, cutting-edge sensors and learning algorithms may require annual audits, calibration, and repairs, just as traditional sensors would. Active Demand ManagementUnder ADM, traveler choices can be influenced by access to the right information. In many cases, this information can be improved and/or optimized by emerging technologies and data. In the Stanford CAPRI study described later in this Reference,(13) commuters were successfully incentivized to re-distribute their departure times in ways that were far more efficient for the overall surface network. In addition to an innovative incentives structure, the program used emerging technologies such as radio frequency identification (RFID) sensing, smartphone applications, and social media. In theory, the traffic flow incentives and monetary awards could be further optimized by a fusion of ML and performance monitoring. In another example, automatic passenger counters (APC) and AVL data have been used to optimize the supply and demand for public transit. The essential idea is to fully utilize the big data in public transit to provide travelers fine-grained, customizable information regarding transit service performance (efficiency, reliability, and quality). This information can be distributed via DMSs at transit stops or on smartphone applications. An example of such information is shown in figure 25. Moreover, transit providers can monitor day-to-day transit service, and can monitor how transit users respond to information. They can develop a better understanding of travelers' preferences on efficiency, reliability, and quality of transit service, as well as their modal choices. Big data and data-driven behavioral models facilitate agencies' decision making (such as scheduling). Effective information provision, along with data-driven scheduling, holds great potential to improve the service performance and travelers' riding experience. 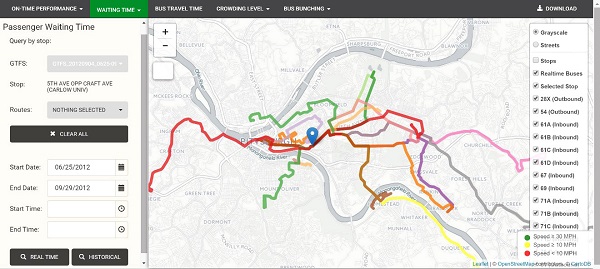 This screenshot shows a map with a pushpin showing the location of the user. Outwards from the user location, a number of color coded transit routes are shown. The color coding for each route indicates the speed of traffic flow along the designated route. On the right side of the map are a number of selection buttons that control what is shown on the map, such as the coloring of the map, the ability to display streets, and the ability to show real-time busses, transit stops, and specific routes. ON the left side of the screen is a passenger waiting time panel that gives the user the ability to query the system for a specific stop using General Transit Feed Specification, and routes. The selected stop is labeled as well. Users can specify a start date and time and an end date and time. There are buttons to clear all waiting time data, and to display information in real time or for historical data.
This screenshot shows a map with a pushpin showing the location of the user. Outwards from the user location, a number of color coded transit routes are shown. The color coding for each route indicates the speed of traffic flow along the designated route. On the right side of the map are a number of selection buttons that control what is shown on the map, such as the coloring of the map, the ability to display streets, and the ability to show real-time busses, transit stops, and specific routes. ON the left side of the screen is a passenger waiting time panel that gives the user the ability to query the system for a specific stop using General Transit Feed Specification, and routes. The selected stop is labeled as well. Users can specify a start date and time and an end date and time. There are buttons to clear all waiting time data, and to display information in real time or for historical data.
Figure 25. Screenshot. Transit passenger wait time.(52) © Pi et al (2017) Regarding O&M issues, RFID, APC, and DMS devices may require physical maintenance and repairs. Similarly, social media data and smartphone applications software may require periodic technical support and software updates. For example, if a social media vendor releases a software update that modifies its input-output format, any data mining tool used to access the social media data will require corresponding updates and software patches. Active Parking ManagementParking can consume a significant amount of the trip costs (time and money) in urban travel. As such, it can considerably influence travelers' choices of modes, locations, and time of travel. Advanced performance monitoring via smart sensors, wireless communication, social media, parking meter transaction data, and big data analytics offers a unique opportunity to tap parking's influence on travel to make the transportation system more efficient, cleaner, and more resilient.(56, 57, and 58) Essentially, these emerging technologies and data sources may facilitate:
Figure 26 illustrates the APM-centric active management cycle. 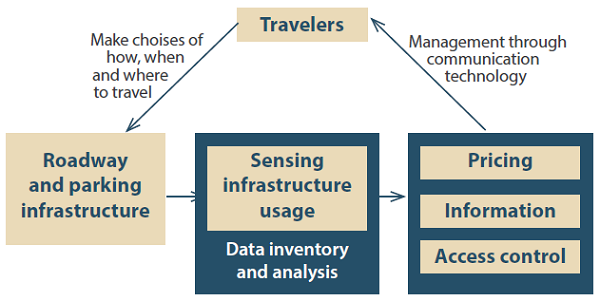 This diagram presents travelers at the top with arrows indicating sending and receiving of information regarding parking. First, a traveler makes choices of how, when, and where to park when planning a trip. This query goes to the roadway and parking infrastructure. At this point, the information is routed to the sensing infrastructure usage system for data inventory and analysis. This information is used to determine pricing, access control and additional information for the specific choices the traveler made. Then, by management through communication technology, this generated information is sent back to the user, completing the cycle.
This diagram presents travelers at the top with arrows indicating sending and receiving of information regarding parking. First, a traveler makes choices of how, when, and where to park when planning a trip. This query goes to the roadway and parking infrastructure. At this point, the information is routed to the sensing infrastructure usage system for data inventory and analysis. This information is used to determine pricing, access control and additional information for the specific choices the traveler made. Then, by management through communication technology, this generated information is sent back to the user, completing the cycle.
Figure 26. Diagram. Enhancement of active parking management using technologies and data. Source: FHWA Regarding O&M issues for APM, the quantity and location of available parking spots is constantly changing. Any cyber-physical system based on parking data will require constant updates. Social media platforms and parking meter transaction data are subject to software updates. Wireless communication technologies are not static. To combat these instabilities, there is a need for human audits, post-deployment monitoring, and dedicated O&M budgets. ML, which represents an automated form of audits, is also highly advisable to complement and support any human audits. Depending on the success of the automated monitoring system, the expenses associated with having humans in the loop may dissipate over time as the human effort decreases accordingly. EnforcementLaw enforcement opportunities and capabilities are evolving along with the new technologies. This has ramifications for ATM and APM. The typical ADM applications (e.g., dynamic ridesharing, on-demand transit, dynamic pricing, predictive traveler information) may not have significant enforcement concerns. One prominent issue is traffic violations involving CAVs. These vehicles could potentially be programmed to avoid speed limit violations, parking violations, red light running, and usage of closed lanes. An increasing market penetration rate of such vehicles could significantly reduce the burden of law enforcement. However, there are many privacy issues associated with CAVs. The driving public will not necessarily accept unfettered control of their driving behaviors and identification of their whereabouts. Therefore, the enforcement impact of CAV technology remains uncertain. Active Traffic ManagementAdaptive ramp metering and traffic signal control strategies can now be deployed on freeways and arterials. Red light running and speed limit violations are two enforcement concerns related to traffic signals, regardless of deployment location. While CAVs may help to prevent such violations, automated traffic signal performance measures may reveal such violations from conventional vehicles and drivers. Automated vehicle or license plate identification may streamline the enforcement process. Two other ATM solutions affect which lanes drivers may use. Dynamic lane and shoulder use allow for temporary opening or closing of travel lanes in response to increasing congestion or incidents. Dynamic junction control prioritizes the critical roadway to minimize the impact of merging and diverging maneuvers. In these cases, illegal use of a closed lane becomes an enforcement issue. While CAVs may help to prevent such violations, automated vehicle or license plate identification may again streamline the enforcement process with conventional drivers. The automated identification may be more technologically challenging along lengthy (i.e., up to many miles long) dynamic lanes or shoulders, on which the violating vehicle location is much less certain than at traffic signal stop-lines or stop-bars. Finally, dynamic speed limits may change based on road, traffic, and weather conditions. Speed limit violations are possible. A combination of technologies is needed to identify vehicle speeds (not necessarily in real-time) and identify the violating vehicles or drivers. Again, the frequency of speed limit violations may potentially be reduced by CAV technology. 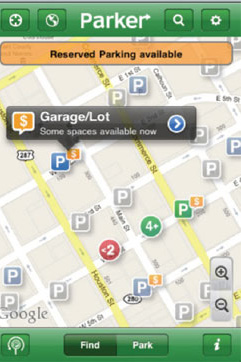
Figure 27. Screenshot. Smartphone parking application. Source: ExpressParkTM Active Parking ManagementAPM solutions can dynamically modify parking spot permissions, prices, and availability. Smartphone applications (e.g., figure 27) that facilitate parking spot payments from remote locations should interface with any APM solutions that may be in effect to prevent unnecessary violations. Automated vehicle or license plate identification may help to reduce law enforcement labor and costs. The frequency of parking violations may potentially be reduced by CAV technology, which can be designed to avoid such violations. However, when APM solutions are in effect, infrastructure-to-vehicle communication may be needed for CAVs to avoid such violations. Costs Associated with Active Traffic ManagementCosts associated with ATM merit consideration long before implementation. Cost data are available through various tools and resources (i.e., TSMO Benefit Cost Compendium,(60) Intelligent Transportation System [ITS] Joint Program Office [JPO] online database,(47, 61, and 62) Tool for Operations Benefit Cost Analysis, Operations Benefit/Cost Analysis Desk Reference to support Tool for Operations Benefit Cost Analysis).(27) Some of the major costs include capital investment into infrastructure, technology, long-term operations, maintenance, and upgrades of the system over time. Usually, the Federal Government provides funding for ATM solutions and projects for both initial construction and ongoing costs. Various Federal Government initiatives provide opportunities for funding ATM solutions individually or along with other activities or projects. State and local level funding are also available. Some ITS infrastructure installations and integrations that may qualify for Federal funds are listed below:
Emerging ATM technologies also require hardware, software, and software integration. Therefore, the long-term support of software, including routine checks and modifications, is a consideration. The integration of CAVs into ATDM solutions will involve implementing advanced infrastructure, which needs to be properly maintained for a longer lifespan. 6.2 Future ProofingA big challenge with technology systems is how to keep them current so they will not need to be constantly updated (often at high costs) as technologies advance. For operational systems such as ATDM, these systems do not need to be quickly obsolete and/or require a replacement shortly after the system is installed. It is difficult in today's quickly moving world of evolving technology to have systems such as these to be truly future-proof, but there are steps that can be taken to help ease the impact of evolving technology. These steps, which are not required, include the following:
|
|
United States Department of Transportation - Federal Highway Administration |
||