Transportation Management Center Information Technology Security
Executive Summary
Cybersecurity is a growing concern worldwide. Over the past several years, much focus has been placed on critical infrastructure providers and their ability to implement cybersecurity in order to continue providing critical services. The Department of Homeland Security considers the Transportation Systems Sector to be 1 of 16 critical infrastructure sectors whose "assets, systems, and networks, whether physical or virtual, are considered so vital to the United States that their incapacitation or destruction would have a debilitating effect on security, national economic security, national public health or safety, or any combination thereof." The cybersecurity threat landscape is constantly evolving, and new vulnerabilities are discovered every day. Connectivity between different networks, organizations and devices, through the Internet of Things (IoT), further increase exposure to these vulnerabilities.
The material within this report has been developed based on best practices (chapter 3) within the industry that correspond to what Traffic Management Centers (TMC) face on a routine basis, pushing for improvements where necessary, and with a primary focus on the National Institute of Standards and Technology (NIST) Cybersecurity Framework and Center for Internet Security (CIS) Top 20 Controls version 7.1. Through this report, TMCs will gain insight into basic practices that all TMCs should adopt as a starting point or baseline for organizations with limited resources and cybersecurity expertise, as well as guidelines for TMCs looking to increase their system maturity. This report also includes guidelines relevant to personnel controls and elements associated with insider vulnerabilities, and covers controls associated with data protection and resiliency. In chapter 3, an assessment of best practices from TMC operators around the country have been summarized and compared with relevant CIS Top 20 Controls. Additionally, areas of needed improvement have been noted based on controls and policies that are not as mature within the TMC industry.
While synthesizing the available resources on Information Technology (IT) cybersecurity, sources from the Department of Homeland Security (DHS), CIS, and NIST were considered for their relevance to TMCs. The NIST Cybersecurity and Risk Management Frameworks were more abstract and strategic in nature, while the CIS Top 20 Controls provide more technical detailed guidelines of immediate benefit to TMC operators. Therefore, using the CIS Top 20 Controls in baselining security measures provides an immediate impact on guiding control of hardware, software and networks in the TMC, while the NIST frameworks can play a beneficial role to supplement with strategic visioning of Risk Management Plans and Resiliency Plans. The following figure depicts the control framework associated with the CIS Top 20 Controls, which have been identified to be the most relevant for TMCs among the reviewed frameworks.
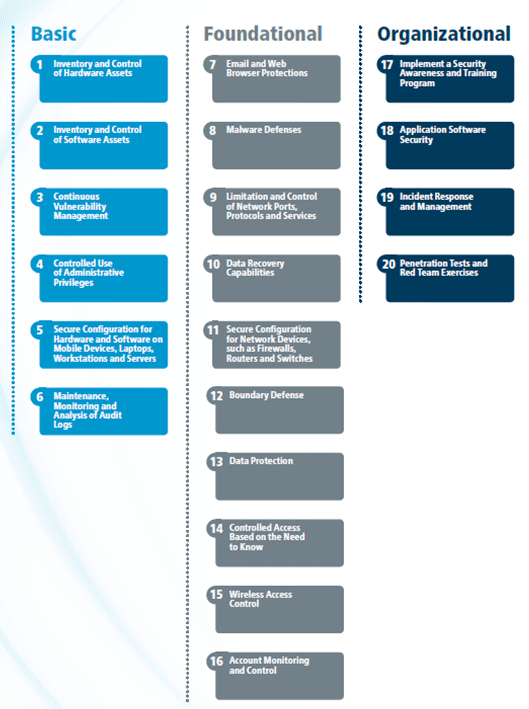 Figure 1. Chart. Center for Internet Security top 20 critical security controls version 7.1.
(Source: CIS Controls Version 7.1.)
Figure 1. Chart. Center for Internet Security top 20 critical security controls version 7.1.
(Source: CIS Controls Version 7.1.)
The CIS Top 20 Controls are the primary focus of the balance of these guidelines and are discussed in context of applicability to TMC roles. A TMC environment, along with supporting staff, is typically comprised of individuals with distinct roles focused on managing three areas:
- Information technology/systems (subdivided to address networking, devices, hardware, and software).
- Personnel (i.e., human resources).
- Administrative and contractual data management practices (e.g., Freedom of Information Act (FOIA) requests, data archival and organizational resiliency, etc.).
The CIS Top 20 Critical Security Controls correspond to these three functional areas, and each CIS sub-control is relevant to one of the three TMC roles, illustrated in the figure below. They have been color-coded to match the Basic, Foundational, and Organizational control labeling in the CIS document figures.
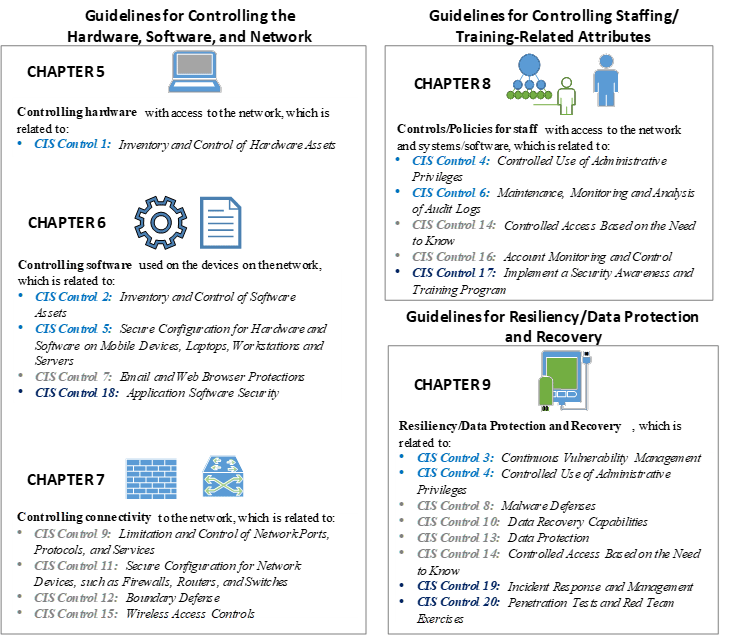 Figure 2. Chart. Relationship between Center for Internet Security Controls and Traffic Management Center roles.
(Source: Federal Highway Administration.)
Figure 2. Chart. Relationship between Center for Internet Security Controls and Traffic Management Center roles.
(Source: Federal Highway Administration.)
The focus areas of each chapter of this document is depicted in the figure above. Chapter 5 emphasizes elements of controlling hardware with access to the network, while chapters 6 and 7 focus on controlling software and network connectivity, respectively. Chapter 8 focuses primarily on personnel and account privileges/controls, and chapter 9 covers the CIS Controls that address improving resiliency and data protection aspects of TMC IT and Operations.
Following the discussion of the Guidelines, chapter 10 presents recommended short- and long-term strategies for implementation such as conducting a self-assessment Cybersecurity Resilience Reviews (CRR) using DHS' CRR tools, conducting a risk analysis, and implementation Basic and Foundational controls to address the immediate risks identified.
Chapter 11 identifies some key conclusions and next steps recognizing that TMCs around the Nation will be at differing levels of maturity. Some agencies already will have a jumpstart on cybersecurity issues, while others may be closer to starting from scratch when reading these guidelines. If an agency is starting from scratch, a Risk Analysis is recommended as the first step towards establishing a cybersecurity program for the TMC. In conjunction with addressing immediate risks from the Risk Analysis, TMC agencies will benefit from developing a Risk Management Plan, as noted in chapter 9, to determine courses of action to mitigate and systematically manage those risks.
Part of increasing the cybersecurity maturity of an agency involves incrementally building a more robust process/program for resiliency by developing a Resiliency Plan to harden systems and facilities to improve the ability to recover from an attack or breach.
Finally, TMC operations staff are encouraged to collaborate on the risk analysis with IT staff. The cooperative panel of Operations Technology (OT) and IT staff should lead the charge on routinely testing and improving the program to address existing and newly identified risks. The panel is encouraged to participate in/with peer groups (i.e., Information Sharing and Analysis Centers (ISAC) as noted in chapter 9) to share and learn from identified threats/risks within the TMC community to allow all TMC operators to learn and benefit from the greater body of knowledge.